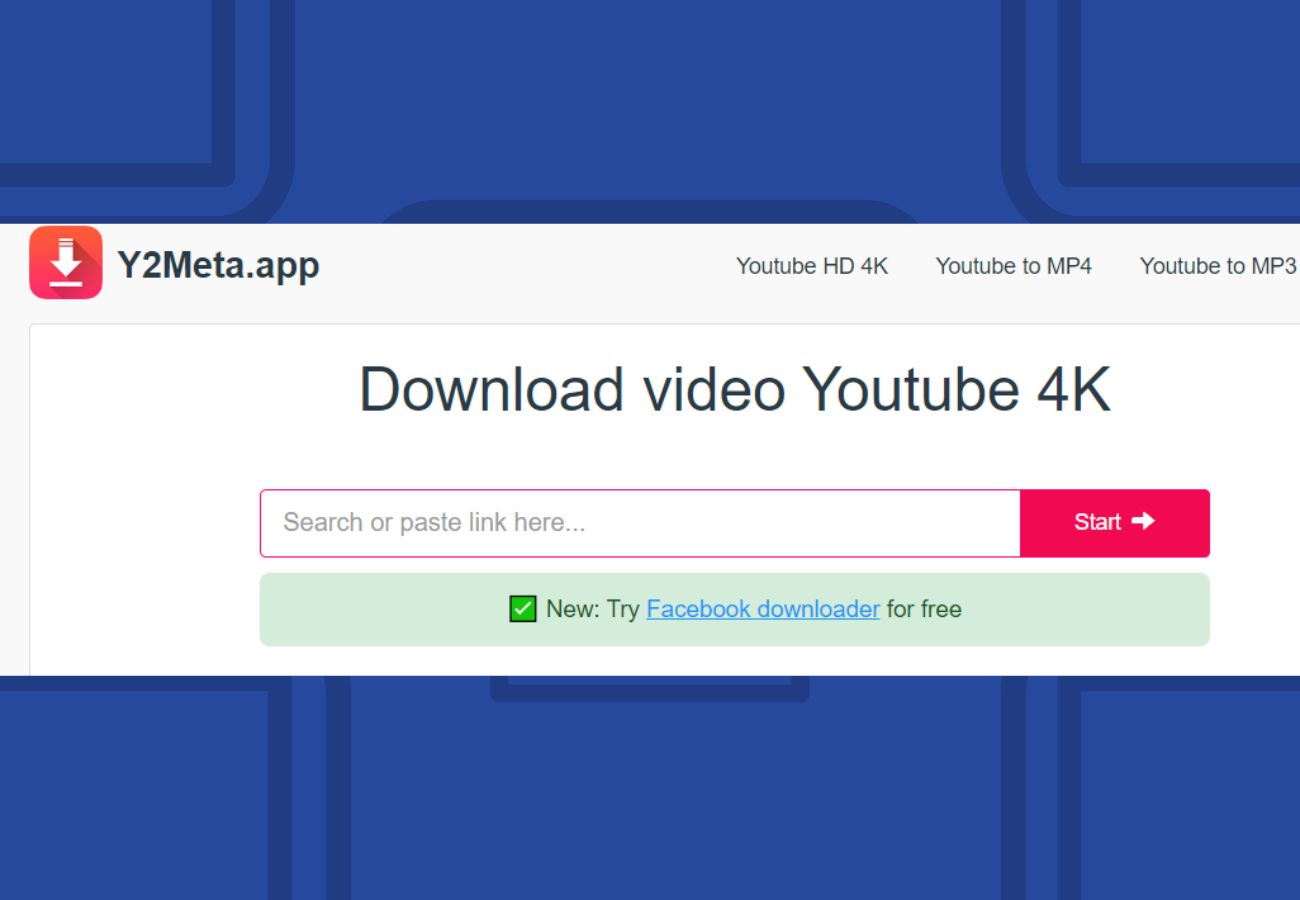
What Is Y2meta And What Is It Used For? Is It Safe?
Y2meta is used to download & Convert video from YouTube, Facebook, Instagram, etc. to Mp3, Mp4 in HD. Y2meta converter for MAC, iOS, Android and Windows will allow you to accomplish just that. Anyone can download videos on YouTube without any hassle with the help of the y2meta tool, a free internet converter. Video files…